Powershell Open Id Connect Login to Web Api
You can integrate with Microsoft Azure Agile Directory (Advertisement) if you desire to let users:
-
From within your company utilise your awarding from an Azure Advertisement controlled by you lot or your organization.
-
From other companies' Azure ADs use your application. (We recommend that you lot configure external directories as unlike connections.)
Prerequisites
-
Register your app with Auth0
-
Select an appropriate Application Type.
-
Add an Allowed Callback URL of
https://YOUR_APP/callback. -
Make certain your Application's Grant Types include the appropriate flows.
-
-
Have an Azure business relationship. If you don't, you can sign upward for gratuitous.
-
Have an Azure AD directory. If you don't, you can create i past post-obit Microsoft's Quickstart: Create a new tenant in Azure Active Directory - Create a new tenant for your arrangement.
Steps
To connect your application to Azure AD, you must:
-
Register your app with Azure AD
-
Create an enterprise connection in Auth0
-
Enable the enterprise connection for your Auth0 Application
-
Exam the connectedness
Annals your app with Azure Advert
To register your app with Azure Advertizing, run into Microsoft'south Quickstart: Annals an awarding with the Microsoft identity platform.
During registration, configure the following settings:
| Selection | Setting |
|---|---|
| Supported account types | To allow users from external organizations (like other Azure Advertizement directories) choose the advisable multitenant pick. Multitenant options include the following: Accounts in whatever organizational directory (Any Azure AD directory - Multitenant). |
| Redirect URI | Select a Redirect URI type of Web, and enter your callback URL: https://YOUR_DOMAIN/login/callback. |
Detect your Auth0 domain name for redirects
If your Auth0 domain proper noun is non shown above and y'all are non using our custom domains feature, your domain name is your tenant name, your regional subdomain (unless your tenant is in the US region and was created earlier June 2020), plus.auth0.com. For case, if your tenant name wereexampleco-enterprises, your Auth0 domain name would beexampleco-enterprises.united states.auth0.com and your redirect URI would behttps://exampleco-enterprises.us.auth0.com/login/callback. (If your tenant is in the United states and was created before June 2020, and so your domain proper name would behttps://exampleco-enterprises.auth0.com.)
If you lot are using custom domains, your redirect URI volition have the following format:https://<YOUR CUSTOM DOMAIN>/login/callback.
During this process, Microsoft generates an Application (customer) ID for your awarding; you tin observe this on the app's Overview screen. Make note of this value.
Create a client hole-and-corner
To create a client secret, see Microsoft's Quickstart: Configure a customer application to admission web APIs - Add Credentials to your web application.
Once generated, make note of this value.
Add permissions
To add together permissions, see Microsoft'southward Quickstart: Configure a customer application to access web APIs - Add permissions to access spider web APIs.
While configuring permissions, consider the post-obit:
If you want to enable extended attributes (such every bit Extended Contour or Security Groups), then you will need to configure the following permissions for the Microsoft Graph API.
| Delegated Permissions | Description |
|---|---|
| Users > User.Read | And then your app tin can sign in users and read the signed-in users' profiles. |
| Directory > Directory.Read.All | So your app can read directory information on the signed-in user's behalf. |
Create an enterprise connection in Auth0
Create and configure an Azure AD Enterprise Connection in Auth0. Make sure you accept the Awarding (client) ID and the Customer hugger-mugger generated when you set upwards your app in the Microsoft Azure portal.
-
Navigate to Auth0 Dashboard > Authentication > Enterprise, locate Microsoft Azure AD, and select its
+.
-
Enter details for your connection, and select Create:
Field Clarification Connection name Logical identifier for your connection; information technology must exist unique for your tenant. Once prepare, this proper noun tin can't be changed. Microsoft Azure Advertizement Domain Your Azure AD domain name. You tin detect this on your Azure Advert directory's overview folio in the Microsoft Azure portal. Client ID Unique identifier for your registered Azure AD awarding. Enter the saved value of the Application (customer) ID for the app you just registered in Azure AD. Client Hugger-mugger Cord used to proceeds access to your registered Azure Advertizing application. Enter the saved value of the Client underground for the app you just registered in Azure AD. Use common endpoint (Optional) When enabled, your application volition dynamically accept users from new directories. Typically enabled if y'all selected a multi-tenant pick for Supported account types for the application you just registered in Azure AD. When enabled, Auth0 will redirect users to Azure'southward common login endpoint, and Azure will perform Domicile Realm Discovery based on the domain of the user's email address. Identity API API used past Auth0 to interact with Azure AD endpoints. Acquire well-nigh the differences in behavior in Microsoft's Why update to Microsoft identity platform (v2.0) doc. Attributes Bones attributes for the signed-in user that your app tin access. Indicates how much information you desire stored in the Auth0 User Contour. Extended Attributes (optional) Extended attributes for the signed-in user that your app tin access. Auth0 APIs (optional) When selected, indicates that we require the ability to make calls to the Azure Advert API, which allows us to search for users in the Azure Advertisement Graph even if they never logged in to Auth0. Sync user profile attributes at each login When enabled, Auth0 automatically syncs user contour information with each user login, thereby ensuring that changes fabricated in the connectedness source are automatically updated in Auth0. Email Verification Choose how Auth0 sets the email_verifiedfield in the user profile. To learn more, meet Email Verification for Azure Advertising and ADFS.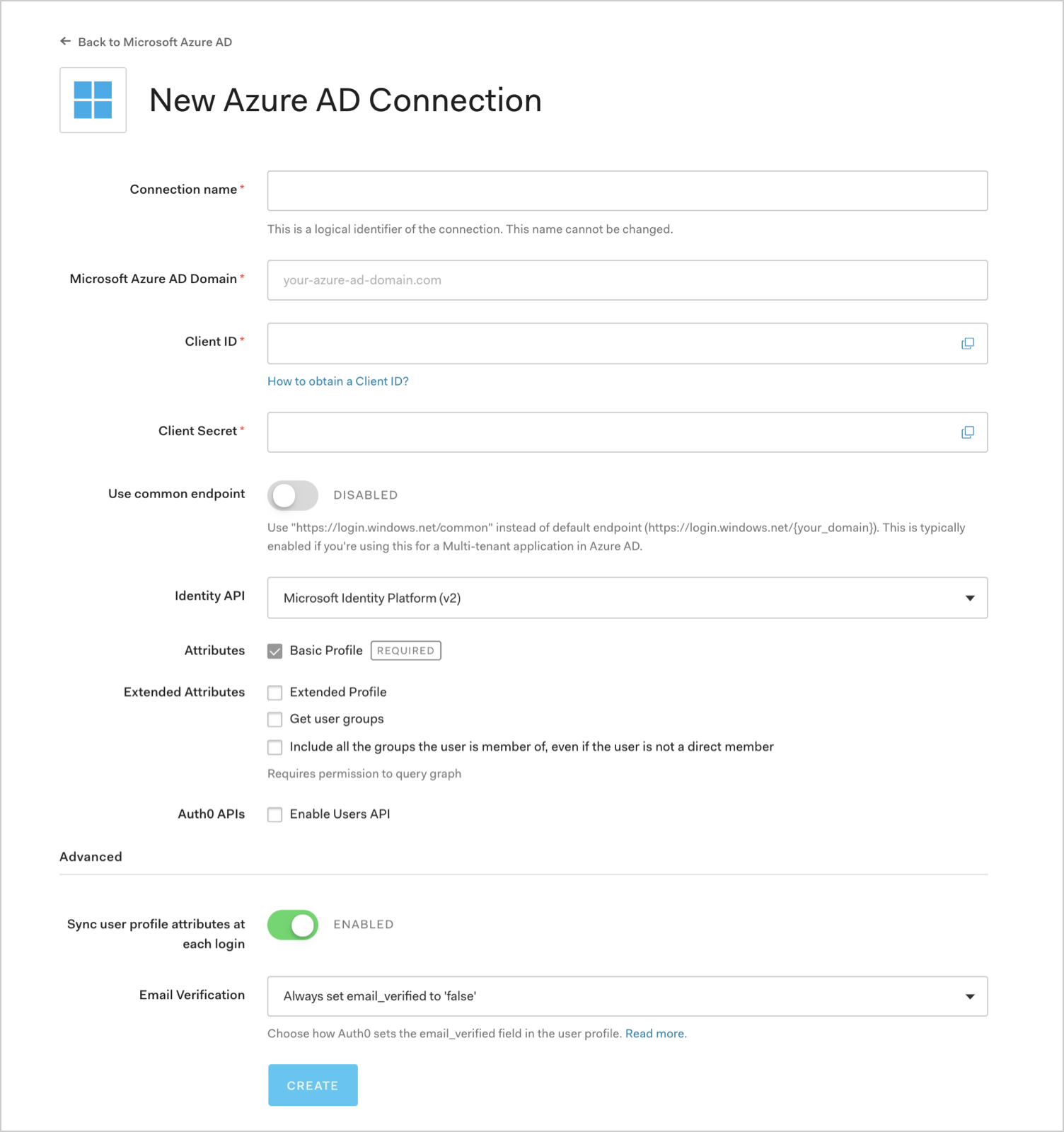
-
In the Login Experience view, you lot tin configure how users log in with this connection.
Field Description Identity Provider domains A comma-separated listing of the domains that tin be authenticated in the Identify Provider. This is only applicable when using Identifier First authentication in the Universal Login Feel. Add push (Optional) Display a push button for this connection in the login folio. Push button display name (Optional) Text used to customize the login button for new Universal Login. When set the button reads: "Go along with {Button brandish name}". Push logo URL (Optional) URL of epitome used to customize the login button for new Universal Login. When set, the Universal Login login push displays the image as a 20px past 20px square. -
If you have appropriate Azure AD administrative permissions to requite consent to the application so users tin log in, and so click Continue. You lot volition be asked to log in to your Azure Advertizement account and give consent. Otherwise, provide the given URL to your administrator so that they can requite consent.
Enable the enterprise connection for your Auth0 awarding
To utilise your new Azure AD enterprise connection, you must first enable the connection for your Auth0 Applications.
Test the connexion
Now yous're set to test your connection.
Troubleshooting
Here are some troubleshooting tips:
I registered my awarding with Azure Advertising, but when I go back to my Azure Active Directory App registrations, I tin can't run into my application.
You may have accidentally registered your app in the incorrect Azure AD directory (or not have created an Azure AD directory at all earlier registering your app). It's likely easiest to re-register your app in Azure AD. Make sure you lot are in the correct directory when you register the app. If you demand to create an Azure AD directory, follow Microsoft'due south Quickstart: Create a new tenant in Azure Active Directory - Create a new tenant for your organisation.
I receive the post-obit error message: "Access cannot be granted to this service because the service listing is non properly configured past the publisher".
To resolve this, attempt changing the Supported account types for your registered Azure Advertisement app. Make sure you have called an appropriate multitenant option in the Azure Advert app's Authentication settings. Multitenant options include the following: Accounts in whatsoever organizational directory (Any Azure AD directory - Multitenant).
When users try to log in, we receive the post-obit error message: "invalid_request; failed to obtain access token".
The well-nigh probable reason for this error is an invalid or expired Azure Advertisement Client secret. To resolve this, generate a new Client underground for your app in Azure Advertizement, and then update the Client Secret in the enterprise connexion configured with Auth0.
Signing Key Rollover in Azure Ad
Signing keys are used by the identity provider to sign the hallmark token information technology bug, and past the consumer application (Auth0 in this case) to validate the authenticity of the generated token.
For security purposes, Azure Advert's signing key rolls on a periodic basis. If this happens, you exercise not need to take any action. Auth0 will use the new cardinal automatically.
Remove unverified label
If yous're using a custom domain, the awarding consent prompt for Azure Ad login may label your domain as "unverified". To remove the unverified label:
-
Verify the domain for the Auth0 application: Add your custom domain name using the Azure Active Directory portal.
-
Assign the verified domain to the Auth0 awarding: How to: Configure an application's publisher domain.
Side by side Steps
-
Integrate with Auth0 using one of our libraries
-
Integrate with Auth0 using our Authentication API
-
Read more about the authentication period
-
Laissez passer additional parameters to the Identity Provider
-
Re-prompt users for permissions
Powershell Open Id Connect Login to Web Api
DOWNLOAD HERE
Source: https://auth0.com/docs/authenticate/identity-providers/enterprise-identity-providers/azure-active-directory/v2
Posted by: 3news2onlinea.blogspot.com
comment 0 comments
more_vert